The Managed Service Provider (MSP) brings a meticulous eye for detail and a knack for deciphering even the most cryptic cyber clues. They tailor their defenses with precision, anticipating threats that others might overlook based on a deep familiarity with their client’s business.
The Cloud Service Provider (CSP) provides the robust infrastructure and standardized security protocols essential for protecting the broader cloud landscape.
However, their focus may be less individualized. To achieve ongoing threat mitigation, businesses must wisely navigate this partnership, understanding when to call upon the expertise of the MSP and CSP.
Businesses too often find themselves amidst a cyber mystery: suspicious logs, unexplained activity, ransomware, and the looming threat of a devastating attack.
The MSP dives deep into these digital clues. They offer analysis and tailored solutions so often lacking in the broader, standardized approach of the CSP.
The Case of The MSP
Businesses seeking comprehensive and personalized cybersecurity solutions often turn to MSPs. These firms deliver proactive security measures and in-depth expertise, offering various services to protect critical assets.
MSPs offer a wide range of security options, such as:
- Comprehensive Security Services: MSPs typically provide hands-on, comprehensive security services that can include managed firewalls, endpoint protection, email security, and threat intelligence. They often take a proactive approach to managing and monitoring the security posture of their client’s IT environments.
- Customization and Flexibility: Security services from MSPs are highly customizable, allowing businesses to tailor their security measures to fit their specific needs, risks, and compliance requirements. This can be beneficial for companies with complex or unique IT environments.
- Partnership and Expertise: MSPs act as an extension of a business’s IT team, offering expertise and resources that the business may not have in-house. This partnership can be crucial for businesses that lack the time or expertise to manage their security needs effectively.
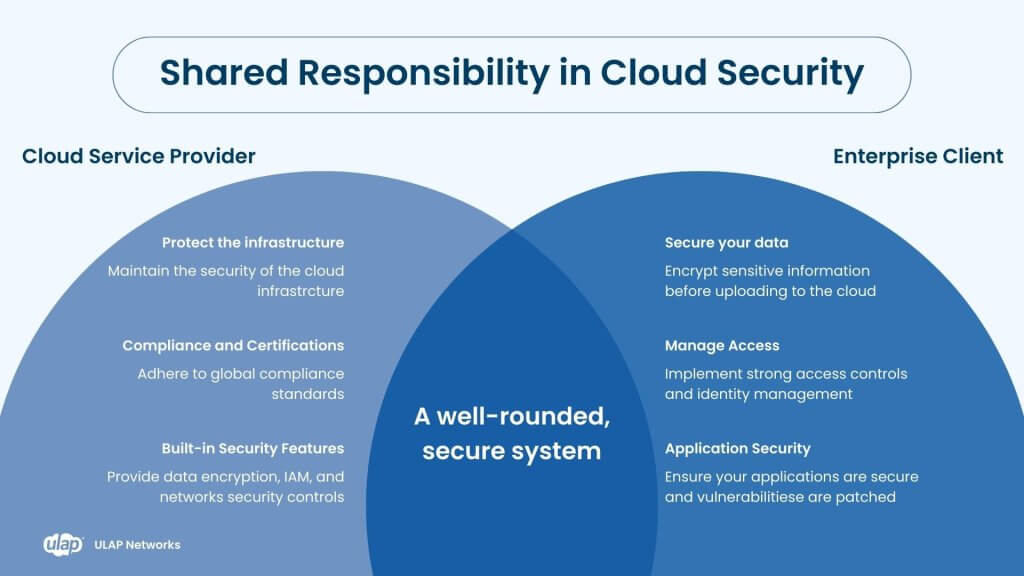
The Case of Shared Responsibility
In the CSP model, the customer holds a significant amount of responsibility within the shared security framework. The CSP provides the foundational cloud infrastructure, while the customer secures their layer on top of it – their data, applications, users, and how they utilize the cloud services. Examples of major CSPs include Amazon Web Services (AWS), Google Cloud Platform, and IBM Cloud. High level features include:
- Security Model: The shared responsibility model is a cornerstone of CSP security, delineating what the provider secures (the cloud infrastructure) and what the customer must secure (data, applications, and identity).
- Built-in Security Features: CSPs offer robust built-in security features, including data encryption, identity and access management (IAM), network security controls, and compliance certifications. These features are designed to protect the infrastructure and services they offer, leveraging their scale and expertise.
- Compliance and Certifications: A key aspect of CSP security is adherence to global and regional compliance standards, which can significantly ease the burden on businesses needing to meet various regulatory requirements.
Final Thoughts
Choosing between or combining the services of MSPs and CSPs is a strategic decision that requires careful assessment. CIOs and IT managers should weigh their organization’s unique needs, risk tolerance, and internal resources.
Key considerations include the desired level of control over security, the size and complexity of the company’s IT environment, in-house security expertise, and compliance requirements.
A hybrid approach that leverages both CSPs for cloud infrastructure and MSPs for specialized security services is often a wise strategy.
It’s not a matter of if your business will be a victim of a cyberattack. It’s a question of when. Protecting against it is a constant effort. By understanding the strengths and limitations of CSPs and MSPs, IT managers can make informed decisions to build a robust cybersecurity posture that helps safeguard their businesses in the ever-evolving threat landscape.